Holding the key to access to Level 11...
"Cookies are protected with XOR encryption" is the message tells by the page... so I guess something has to be done with the cookies... So, I proceed with the source codes...
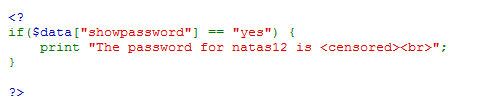
Simply enough, I know that when the value of "showpassword" in the key "data" returns True, the page will display the password for the next level... so I have to understand the algorithm that create the value "yes" for the "showpassword"...
The PHP codes will then perform json_encode with the data, followed by encrypt with XOR and encode with base64 encryption... so, basically what I need to do is to find the key for the xor encryption process and reverse the whole progress to generate a brand new cookie value...
From the loadData(), I know that the progress flow is like this:
base64_decode => xor_encrypt => json_decode
And it will encode the value before passing for verification using the flow:
json_encode => xor_encrypt => base64_encode
Obtained my cookie's data value through BurpSuite proxy... and I proceed with a new php to find out the key value...
Since, A XOR B = C and C XOR B = A...
So I do it in a reverse way by decode the "data" value with base64, followed XOR encryption and json_decode...
Execute the PHP file will returns with a key, which is "qw8J" in repeated form...
Reproduce the cookie's data value by changing the "showpassword" value to "yes" and generate the required cookie value...
Replace the cookie using BurpSuite...
And, the page returns with the password for Level 12...
Natas12 allows me to upload a JPEG file... so, I am thinking whether I can upload some php code to `echo` the password content... Again, I look into the source code through the provided link...
Seems like the upload form is not sanitized... so I quickly upload a simple backdoor php file, which can be found in the Kali linux itself... at the same time, running together with BurpSuite...
I changed the file name into "backdoor.php"... and forward the traffic... the page will then returns the message for upload successful and the link to the uploaded file... the uploaded filename is replaced with some randomly generated strings name... so, `cat` command to display the content of "/etc/natas_webpass/natas13" on the page itself...
Copy the password and ready to move onto Natas13...
Natas13 is the exactly same as Natas12, except Natas13 is smarter this time by limiting the upload form to accept only the image files...
However, all the image file has their respective magic numbers in front to indicate themselves as the image file rather than mp3 file or others...
I simply screenshot on my screen and dump the hex value of the screenshot image file, which happens to be a PNG file...
The very first 8 bytes from the hex dump value, we can see that the magic number for a PNG file...
So, by using the 8 bytes magic number... I write a simply python script to generate a new php backdoor to bypass the security check...
Double checked on the newly created php backdoor file, and verified that it carry the magic number as a PNG file...
Repeated the whole steps as previous level through BurpSuite...
A message to indicate the file has been uploaded successfully which provided together with a new link to that uploaded php file...
Issue the command on the URL will execute the command itself... and I tend to look for the password located in "/etc/natas_webpass/natas14"...
And, I got the password for the next level access...
Natas14 requesting for username and password...at first glance, I am thinking this would be the SQL injection challenge...
Looking into the code itself proves that my hunch are right...
Login successfully and provied with the password for Natas15...
Natas15 only request for the username unlike the previous level...
Codes are able to tell if any user is exists or not...
So basically, I can perform the blind SQL attack which works like this... if my password are correct and the user exists, returns me a True value, which is "This user exists"... else returns me False...
Well, you get the idea... :)
However, instead of using brute forcing, I tried to use sqlmap helps here...
I know the username natas16 exists, I know the database type, I know the returned strings, and I know the injection type...
After some automated attacks, SQLmap returns with a few credentials found included the credential for natas16...
Natas16 reminds me of Natas10... but I am sure this time the security will be even tighter...
The filter character has been increased... use a simple python script here ...
After some times for brute forcing the 32 characters... it returns the password for Natas17...
Again, Natas17 is something similar to Natas15... so, I will just go for the SQLmap to do the jobs, while I am doing my other daily tasks...
--data "username=natas18"
--dbms=MySQL
--technique=T (Since this would be a time-based blind SQL injection, and it means I got a lot of time to do my other own task too...)
SQLmap does not disappoint me again this time by returning the credential for Natas18...
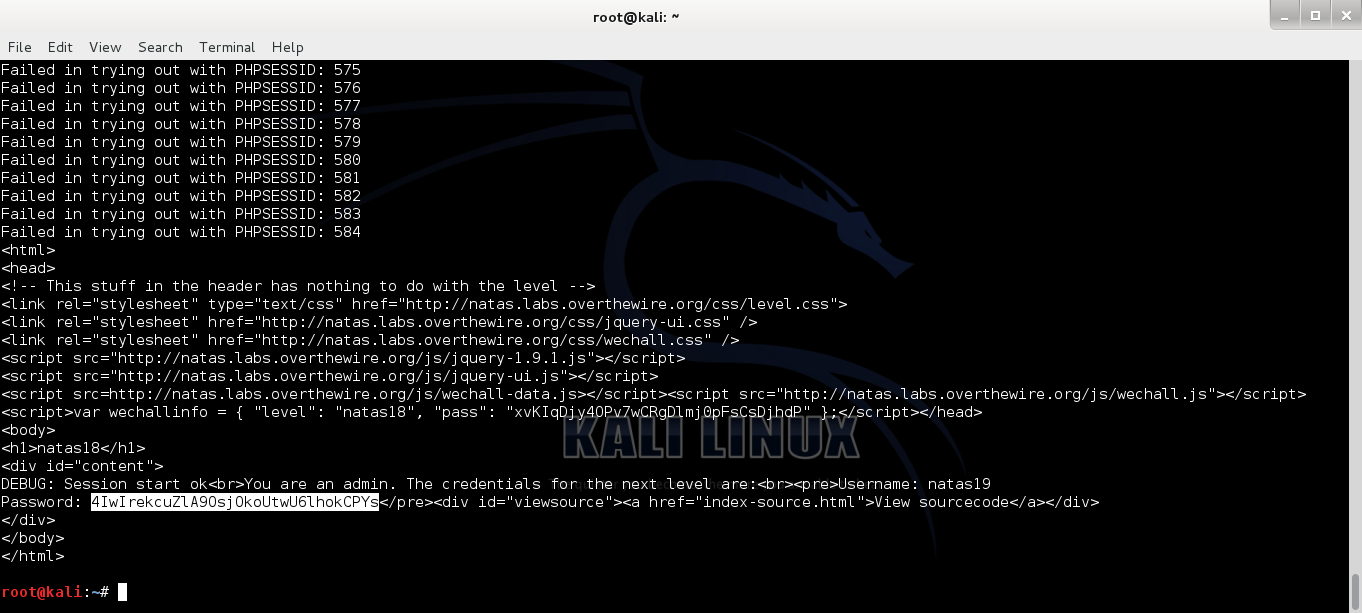
Natas18 requested for admin accounts in order to retrieve the credentials for Natas19... checking out the source code and I know there will be one session id ranging from 0-640 belongs to admin account... brute forcing with 641 attempts doesn't sound bad actually...
Grabbing the password and going for the next level...
Natas19 tells me that this level use mostly the same code as the previous level, but the session IDs are not longer sequential... so, I try to find out the meaning behind this hint using BurpSuite again...

By decoding this, I know that it has an extra "-admin" for the session ID... so I can still use back my previous codes with a little amendment...
Run the python code and it returns with the password for Natas20...
Again, Natas20 requested to be an admin account in order to retrieve the credentials for Natas21... after analyzing the source code and checking out the BurpSuite... I know that the value for parameter "name" is written to the session file... so I just have to create a new "admin" parameter with value "1"...
The password for the next level is returns on the page...
Stay tune for the remaining levels till level 27 which I have already completed... just need some time to post things up...