Hopefully will see some coming challenges to be added on this series again.. :)
For this moment, let's heads on and attack the
This box is running with DHCP enabled... Hence, ping sweep throughout the network is required in order to find out the real ip address of the target box...
Here, we use the Netdiscover in order to find out the ip address of the target box, which is 192.168.17.141
Never forgets to recon the box and grab as much info as possible...
Aggressive mode...
Checking out their website... some quotes by Bill Gates <3 br="">
Seems like nothing we can get from the website (there is a hints section in the website)...
Let's try with Dirbuster and see if we might get some interesting sub-directory....
Some interesting sub-directory founded: forum, phpmyadmin, webmail...
Let's head over the forum section and see what might we get from there...
Oops... some careless mistake done by one of the staff "mbrown" who leaked his own password in the forum... ;)
Let's try login to the forum using 'mbrown' account credentials...
And, we can see his email account after login to his profile...
Since we got an email account, might as well try login to his webmail and see if it is successful...
BOOM! Another password found for the "root" account... XD
From this email, we can find out that "mbrown" using the same password for a several services... (as we can see even from this stage... 'mbrown' is using the same password for his forum and email account... )
Since now we got the 'root' account for phpmyadmin... let's check out the phpmyadmin as well...

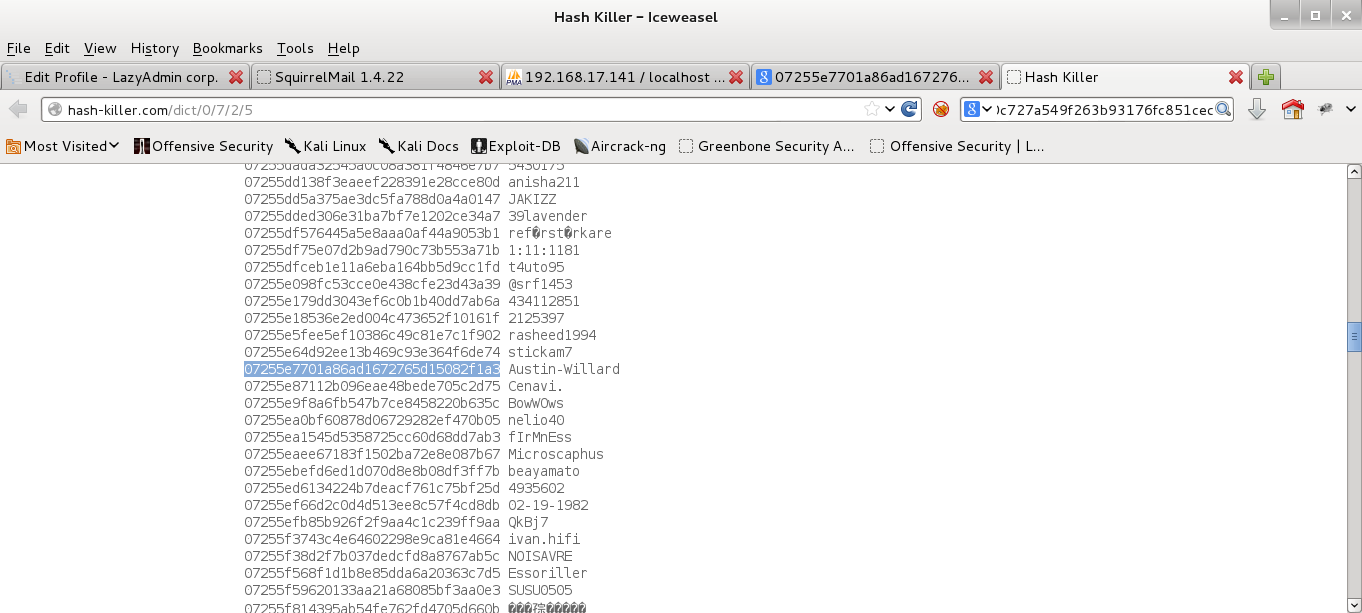
We able to login successfully using the "root" account found... and we can see some password hashes in the database as well... :)
By searching the hash using Google search engine, we can easily
Now, we try ftp into the box using the credentials we found just now...
Fortunately enough, we can still able to access the ftp service successfully using the 'rhedley' account...
By sniffing around for any suspicious files, we see an encrypted file located in the ftp folder... Sadly to tell that we do not have the key to decrypt the file at the moment, but we may download the file to our local box for further usage later...
Seems like we are out of our way to get a shell on the box... :(
After Googling around, we found that /forum/templates_c/ is actually writable... we shed some lights here...
Quickly login into the phpmyadmin, we create a new table 'shell' under the 'test' database..
Generate a php shell payload...
Insert the code into column '1' in table 'shell'...

And insert into dumpfile...
Refresh the page at /forum/templates_c/ and we can see a newly created phpshell.php file... :)
Before running the shell payload, we need to prepare some handler in order
We now have a shell on the target box, but the shell is running with minimal privilege...
Let's try with the 'rhedley' account we found earlier...
Another round of scorching around...
And we found the key to decrypt the encrypted file we retrieved earlier... :)
After decrypt the file, we found that it is actually a copy of 'etc' folder of the target box... now we will need to crack the password in order to get sudo privilege on the box...
By using the darkc0de wordlist, we able to get the password for the 'sraines' account, which is previous account of 'swillard'...
So, let's try change the user to swillard but using the password found for 'sraines'... "brillantissimo"!
Now, we got a proper root shell on the target box... checking out the
A very rewarding challenge... :)