This is one joyful and also one full of frustration box as it took me quite some times to solve it... but it is very rewarding as well... really thanks to superkojiman on this great challenge that he designed... not sure why he named it as Brainpan, but I will definitely named it as Brainpain, which literally explained everything... :)
This challenge is designed solely based on buffer overflow exploitation and it is a good chance for noobie like me to start off and train on... :)
Kick start with finding the target IP...
Scan for the ports...
Returned only 2 open ports, which are 9999 and 10000...
Let's recon harder and see if we can find something better...
Nothing useful...
Check out their http website...
Scrapped the web page source code but nothing found again...
Let's poke on its 9999 port and see what is going to happen...
Obviously not some easy brute force or dictionary attack can break in...
Leave it and move on again...
Check if any sub-directory found on the web hosting...
Found a "/bin" directory...
Let's check it out... :)
Found a "brainpan.exe" file... seems like a Windows executable file...
Grab it down for further probing...
Checked and verified it is a Windows executable file...
Some forensics-fu with 'Strings' command and found the password for port 9999 is "shitstorm"...
Tried log in using the credential found successfully but nothing rewarding so far...
Move the 'brainpan.exe' file over to Windows environment and debug using Immunity Debugger...
At the same end, create a fuzzer script as shown below to fuzz with the "brainpan.exe" file...
Set the target IP address accordingly, here we will set the IP of the windows machine first before we move on back to our Brainpan box...
The script will try feed from 100 bytes and increment of 100 every time until the program crashed... and this is where we begin our buffer overflow exploitation...
Seems like the program crashed after intake of 600 bytes... hence we create a unique 600 bytes to identify the offset of EIP...
Next step is to find the exact offset of EIP using the pattern_offset script in Kali linux...
Since the leftover spaces for shell code is definitely not enough (600-524 = 76 bytes)... We tried to increase it further to 1000 bytes see if the crashed address remained the same...
Well, since the program behave the same if we push in 1000 bytes... so we make changes accordingly...
Push in 524 of "A" + 4 of "B" to differentiate the memory address + the rest bytes will be filled with "C" temporary...
Tested and everything seems fine...
Next step is to find the memory address for "JMP ESP"...
Finding out the hexcode for instruction "JMP ESP" using the nasm_shell scripts...
Execute the mona scripts in Immunity Debugger...
!mona find -s "\xff\xe4" -m brainpan.exe
Replace the memory address found accordingly...
At the other hand, create the payload...
Put the shell code created earlier into our fuzzer scripts...
Padding the shell code with some NOP bytes...
Launch a handler to catch the reverse shell...
Run the exploit and check for the reverse shell...
The attack is successful...
Let's move this back to Linux payload...
Create another new payload using the msfpayload for linux...
Replace the code accordingly...
Launch the exploit as previous attack and wait for reverse shell...
Now, we got a shell on the target box... apparently this user does not have much privilege on the box... let's see what can this user 'puck' do as sudo with "sudo -l" command...
Only one sudo command which does not require any password... "anansi_util"...
This command require at least one argument...
As far as I know, we can launch another shell within the "manual" command...
So here, I try with "manual vi"...
We see a regular manual page for "vi"...
To launch an command within "manual", we pre-pend an "!" in front of it...
Hence, "!/bin/bash" will launch another shell within the "manual"...
Check for the id and we got the root shell instantly... :)
A very nice challenge indeed... sorry as I do not have screenshots from windows machine as I accidentally reverted the machine... :(
Showing posts with label dirbuster. Show all posts
Showing posts with label dirbuster. Show all posts
Friday, June 20, 2014
[WALKTHROUGH] Brainpan 1
Labels:
brainpan,
buffer overflow,
dirbuster,
exploitation,
fuzzer,
immunity debugger,
manual,
mona.py,
msfencode,
msfpayload,
nasm_shell,
netcat,
nmap,
pattern_create,
pattern_offset,
vi,
vulnhub,
walkthrough
Wednesday, May 28, 2014
[WALKTHROUGH] KIOPTRIX Level 4
Here comes the Level 4 of Kioptrix challenge... :))
Let's start off with finding out the IP address of our target box...
Do a ping sweep for the whole Class C network range and output the result in a formatted way using the powerful feature of Nmap itself...
Output the display of the content of the formatted content and grep the necessary info...
Next thing is proceed with the reconnaissance process...
From the results, we know that the box is running several service like SSH, HTTP, and SMB...
SMB is definitely a good point in gathering more information about the target box... :))
Let's do a deeper scan with the aggressive mode in Nmap...
Since we know that the box is hosting some web server, let's head over and see the content of the web page... :)
Reaching the web page of the target, we see a cute little
Tried with the 'admin' with sql injection but ended up unsuccessful... However, it seems that sql injection is possible in this page...
Since we do not have a valid user account to test it out, let's leave it aside for a moment and scan with DirBuster to see if we can find any useful resources... :))
We see some 'usernames' out from the DirBuster results...
Let's try again this time with both the username 'john' and 'robert'... :))

So, now we have the password for user 'john' and 'robert'...
Without further delay, let's login using the credentials found using SSH...
We have successfully get a shell from the target box... however.......
Unfortunately, we have a limited shell and only able to execute some available fixed commands...
After done some Google-fu, we found that lshell is a python based shell and it is able to bypass the restriction IF ONLY 'echo' command or 'vi/vim' command is available...
After bypassing the restriction, we now have a proper shell on the target box...
It is time to search for a local exploit to escalate to root privilege...
After some trial and error, we have found a suitable exploit for the box...
Transferring binary files by wget the file hosting on web server is a little bit tricky...
Hence, we go for another method for file transferring using the Netcat...

After received the exploit file successfully, we change the file permission to highest '777' and by running the exploit, we are able to get a root shell... :))
While I poking around the box, I found a congrats note from the author... :))
And, thank you loneferret... it was fun! :)
Thursday, May 15, 2014
[WALKTHROUGH] De-ICE_S1-140
Seems like this will be the final challenge in De-ICE series... and I really enjoyed myself throughout the full series...
Hopefully will see some coming challenges to be added on this series again.. :)
For this moment, let's heads on and attack thefinal box...
This box is running with DHCP enabled... Hence, ping sweep throughout the network is required in order to find out the real ip address of the target box...
Here, we use the Netdiscover in order to find out the ip address of the target box, which is 192.168.17.141
Never forgets to recon the box and grab as much info as possible...
Aggressive mode...
Checking out their website... some quotes by Bill Gates <3 br="">
Seems like nothing we can get from the website (there is a hints section in the website)...
Let's try with Dirbuster and see if we might get some interesting sub-directory....
Some interesting sub-directory founded: forum, phpmyadmin, webmail...
Let's head over the forum section and see what might we get from there...
Oops... some careless mistake done by one of the staff "mbrown" who leaked his own password in the forum... ;)
Let's try login to the forum using 'mbrown' account credentials...
And, we can see his email account after login to his profile...
Since we got an email account, might as well try login to his webmail and see if it is successful...
BOOM! Another password found for the "root" account... XD
From this email, we can find out that "mbrown" using the same password for a several services... (as we can see even from this stage... 'mbrown' is using the same password for his forum and email account... )
Since now we got the 'root' account for phpmyadmin... let's check out the phpmyadmin as well...

We able to login successfully using the "root" account found... and we can see some password hashes in the database as well... :)
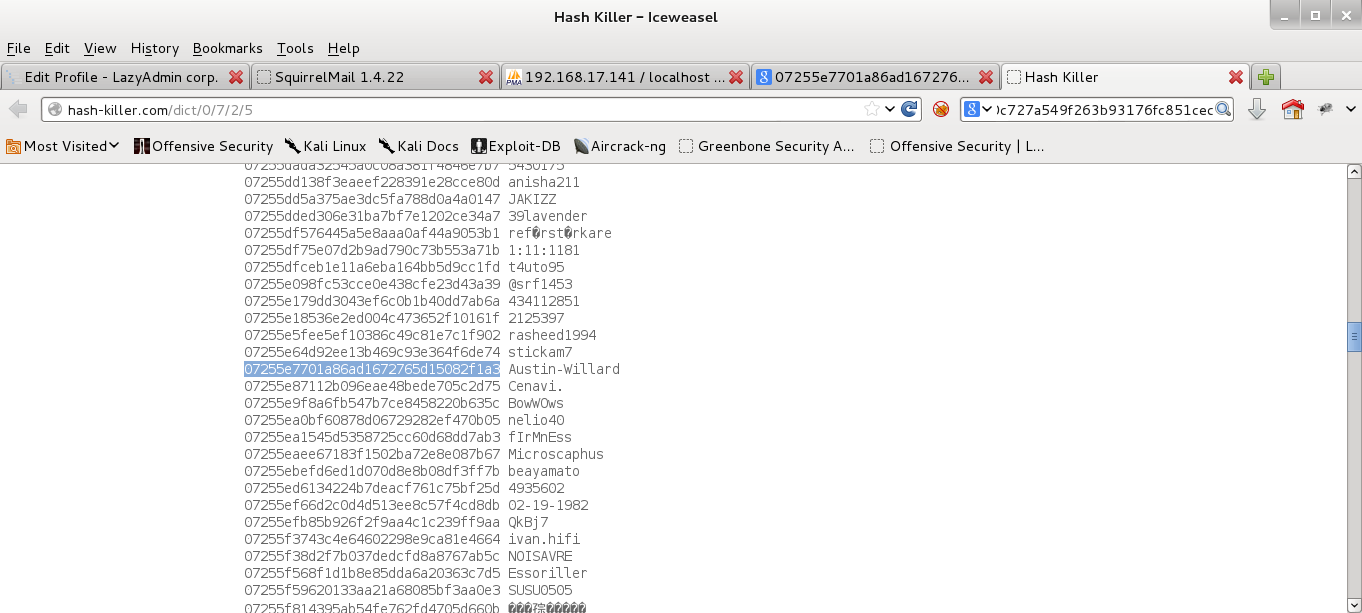
By searching the hash using Google search engine, we can easilycracked found the password for two of the accounts there...
Now, we try ftp into the box using the credentials we found just now...
Fortunately enough, we can still able to access the ftp service successfully using the 'rhedley' account...
By sniffing around for any suspicious files, we see an encrypted file located in the ftp folder... Sadly to tell that we do not have the key to decrypt the file at the moment, but we may download the file to our local box for further usage later...
Seems like we are out of our way to get a shell on the box... :(
After Googling around, we found that /forum/templates_c/ is actually writable... we shed some lights here...
Quickly login into the phpmyadmin, we create a new table 'shell' under the 'test' database..
Generate a php shell payload...

Refresh the page at /forum/templates_c/ and we can see a newly created phpshell.php file... :)
Before running the shell payload, we need to prepare some handler in ordercatch handle the exploit...
We now have a shell on the target box, but the shell is running with minimal privilege...
Let's try with the 'rhedley' account we found earlier...
Another round of scorching around...
And we found the key to decrypt the encrypted file we retrieved earlier... :)
After decrypt the file, we found that it is actually a copy of 'etc' folder of the target box... now we will need to crack the password in order to get sudo privilege on the box...
By using the darkc0de wordlist, we able to get the password for the 'sraines' account, which is previous account of 'swillard'...
So, let's try change the user to swillard but using the password found for 'sraines'... "brillantissimo"!
Now, we got a proper root shell on the target box... checking out theflag secret.jpg and we are rewarded with a cake! :)
A very rewarding challenge... :)
Hopefully will see some coming challenges to be added on this series again.. :)
For this moment, let's heads on and attack the
This box is running with DHCP enabled... Hence, ping sweep throughout the network is required in order to find out the real ip address of the target box...
Here, we use the Netdiscover in order to find out the ip address of the target box, which is 192.168.17.141
Never forgets to recon the box and grab as much info as possible...
Aggressive mode...
Checking out their website... some quotes by Bill Gates <3 br="">
Seems like nothing we can get from the website (there is a hints section in the website)...
Let's try with Dirbuster and see if we might get some interesting sub-directory....
Some interesting sub-directory founded: forum, phpmyadmin, webmail...
Let's head over the forum section and see what might we get from there...
Oops... some careless mistake done by one of the staff "mbrown" who leaked his own password in the forum... ;)
Let's try login to the forum using 'mbrown' account credentials...
And, we can see his email account after login to his profile...
Since we got an email account, might as well try login to his webmail and see if it is successful...
BOOM! Another password found for the "root" account... XD
From this email, we can find out that "mbrown" using the same password for a several services... (as we can see even from this stage... 'mbrown' is using the same password for his forum and email account... )
Since now we got the 'root' account for phpmyadmin... let's check out the phpmyadmin as well...

We able to login successfully using the "root" account found... and we can see some password hashes in the database as well... :)
By searching the hash using Google search engine, we can easily
Now, we try ftp into the box using the credentials we found just now...
Fortunately enough, we can still able to access the ftp service successfully using the 'rhedley' account...
By sniffing around for any suspicious files, we see an encrypted file located in the ftp folder... Sadly to tell that we do not have the key to decrypt the file at the moment, but we may download the file to our local box for further usage later...
Seems like we are out of our way to get a shell on the box... :(
After Googling around, we found that /forum/templates_c/ is actually writable... we shed some lights here...
Quickly login into the phpmyadmin, we create a new table 'shell' under the 'test' database..
Generate a php shell payload...
Insert the code into column '1' in table 'shell'...

And insert into dumpfile...
Refresh the page at /forum/templates_c/ and we can see a newly created phpshell.php file... :)
Before running the shell payload, we need to prepare some handler in order
We now have a shell on the target box, but the shell is running with minimal privilege...
Let's try with the 'rhedley' account we found earlier...
Another round of scorching around...
And we found the key to decrypt the encrypted file we retrieved earlier... :)
After decrypt the file, we found that it is actually a copy of 'etc' folder of the target box... now we will need to crack the password in order to get sudo privilege on the box...
By using the darkc0de wordlist, we able to get the password for the 'sraines' account, which is previous account of 'swillard'...
So, let's try change the user to swillard but using the password found for 'sraines'... "brillantissimo"!
Now, we got a proper root shell on the target box... checking out the
A very rewarding challenge... :)
Subscribe to:
Posts (Atom)