You may want to check out the walkthrough from Natas0 - Natas10 as well...
Here will talks about the walkthrough from Natas21 to the final level...
Granted with the password earlier in Natas20 brings me to Natas21...
A note from Natas21 tells me that this website has a sibling location, which looks like a experimental page... Before going over to Natas21 sibling web page, I peek into the source code...
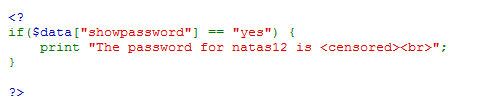
Pretty straightforward... which is required the "admin" parameter with value "1" in the session in order to print out the credentials for next level on the page...
So, I navigate over to the experimenter page... this page prompt for the credentials for Natas21 also... but then again, I already have the password for Natas21. Hence, this will not be a problem for me...
Check out the source code...
Firing up my BurpSuite and add a new parameter "admin" with the value "1"... Forward the packet...
Checking with debug to confirm with the new parameter is added to the session...

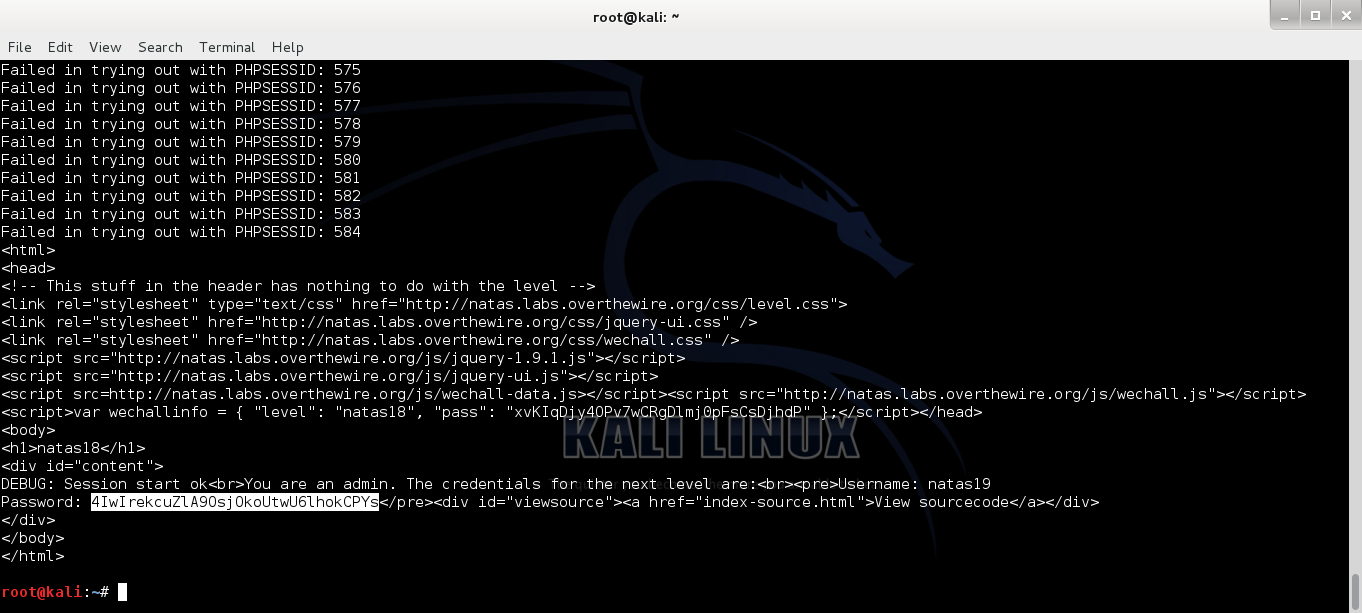
Intercept the traffic with BurpSuite again and copy the PHPSESSID, if you noticed the value changed.... navigate back to the main page and replace the PHPSESSID with the one copied just now...
The main page will returns the password for Natas22...
Natas22 page returns a blank white with a link to source code. Without any doubt, I check on the source code again...
It says only admin can reveal the password... else it will redirect back to the home page... I tried with intercept the traffic with BurpSuite together with the parameter "revelio" and "admin" with the value "1", but it turns out to be failed.
Hence, in order to print out the web content without being redirect, I use the `curl` command...
Combined together with the `grep` command provides a better view for the results...
Natas23 asking for password directly in order to login... but I do not know the pass-phrase. So, I went out checking on the source code to get an idea...
The prompt box is asking for a password contains the word "iloveyou" and the value greater than 10... so I just input the password "11iloveyou" as it contains the keyword "iloveyou" and the int value is greater than 10...
The command "$_REQUEST["passwd"] > 10" does implicit casting a string to int. Basically, "11iloveyou" will become "11" as integer value...
Password is granted!
Natas24 has the similar looks to previous level... check out the source code....
If the input password matched with the censored word, the password for the next level will be printed out. But I do not know the exact censored words...
So I fire up BurpSuite to intercept the traffic again and start fuzzing around... since it is comparing strings value, and what will happens if I pass the data as array to mess things up a little bit?
The page returns with a warning message and also THE KEY for the next password! My guess is that strcmp an array and a string results in an error and returns "False" as the value, since the "!" in front of it negate the returned results and hence become "True" value...
What a long quote displayed on the Natas25 =.=!! Well, I just don't bother to go read it up.
Since I got control over the HEADER and the SESSION ID, I can perform directory traversal attack using the language although it seems to be sanitized...
However, by replacing every "../" with nothing does not help at all...
Because,
"../" => ""
"..././" => "../"
Intercepted the traffic with BurpSuite and trying to display the log file, which is written the password for Natas26 through the HEADER I manipulated earlier...
Get the password and move onto level 26...
Natas26 seems like an image drawer, but it doesn't matter until I look further into its code to seeks for vulnerable point...
The code contained the unserialize() together with the magic method __destruct()... Hence, this might be vulnerable to PHP Object Injection...
I create a php file with Logger class modeled based on the original with some amendments...


Execute the php file and I got the generated cookie value...

Intercepted the traffic with BurpSuite again and input the latest generated cookie value...
Next thing to do is to navigate to the "/img/letmepass.php".
Got the password to the final level... Natas27...
Accessing the Natas27 with the congratulations message... :)